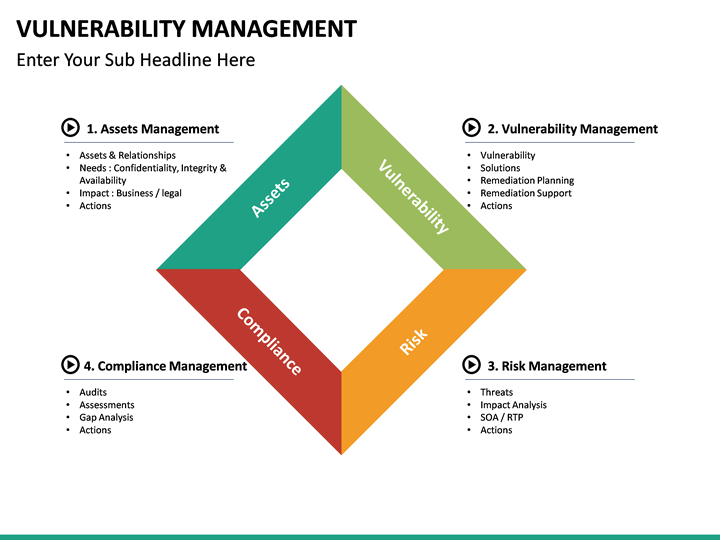
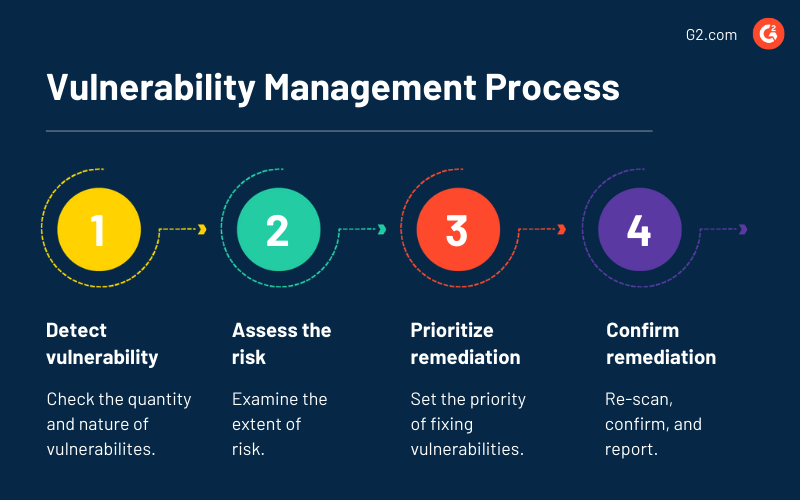
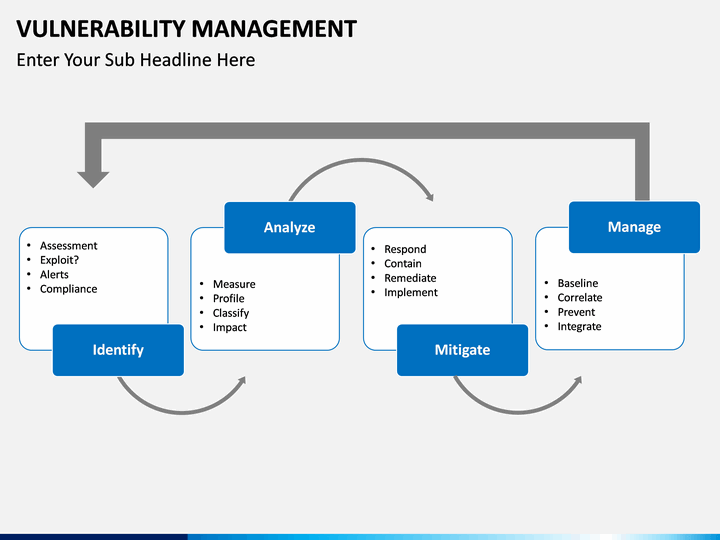
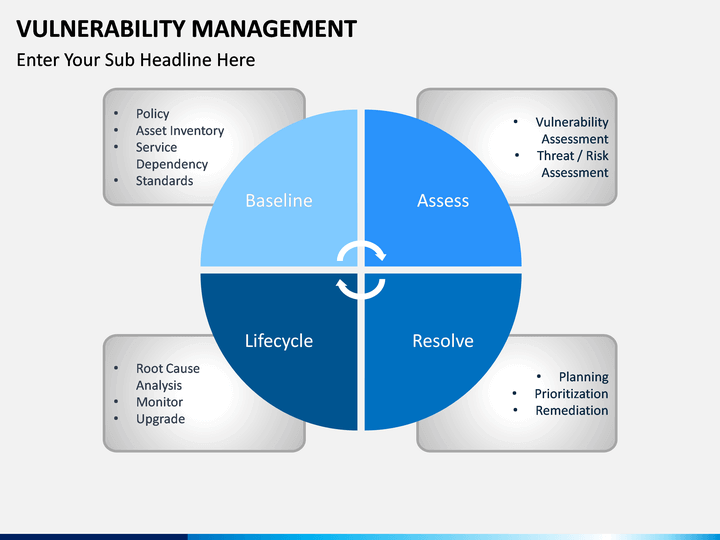
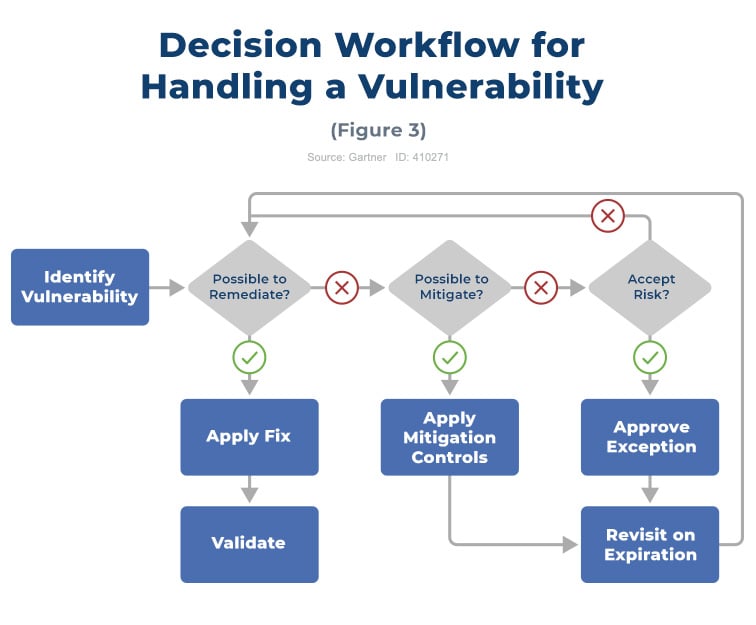
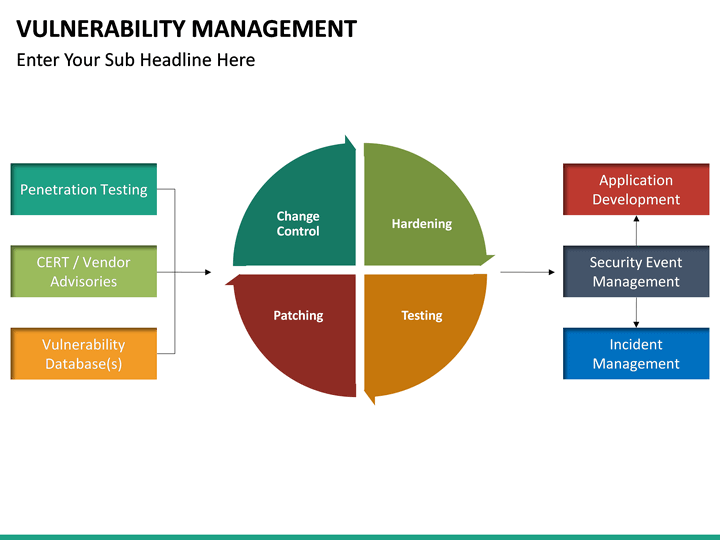
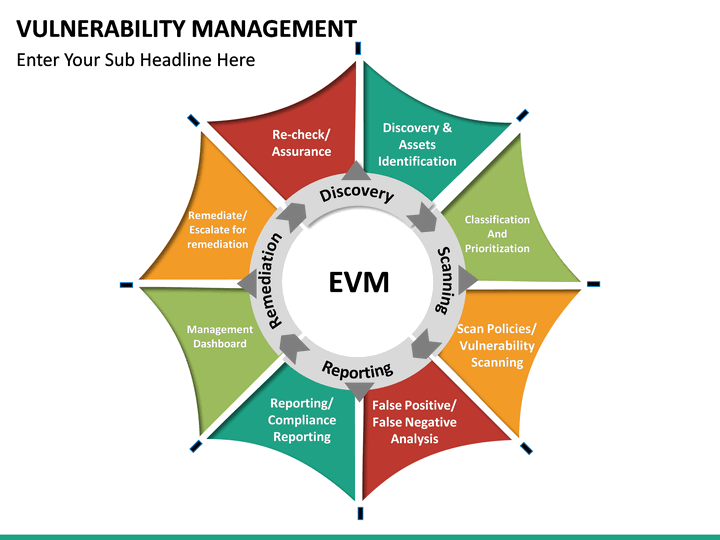
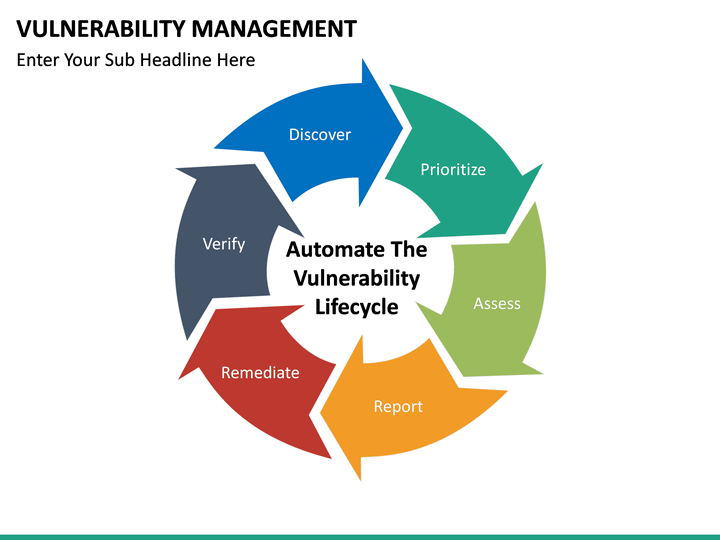
Vulnerability Management Process Template
Vulnerability Management Process Template - Web the guide to resume tailoring. Because new vulnerabilities can arise at any time, security teams approach. Web download our free vulnerability management policy template now. Web vulnerability is defined in the iso 27002 standard as “a weakness of an asset or group of assets that can be exploited by. Web you can easily edit this template using creately. Web this paper looks at how a vulnerability management (vm) process could be designed and implemented within. Stay current with free resources focused on vulnerability management. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. Web guidance to help organisations assess and prioritise vulnerabilities. Once the description is posted, the openstack/ossa or ossa. Web for example, the task “scope” feeds into multiple processes: Web 4 steps of the vulnerability management process. Web the vulnerability management process. Overview 1.1 procedure owner 1.2 classification 1.3 applicable regulations 1.4 related [company]. Web this paper looks at how a vulnerability management (vm) process could be designed and implemented within. Web the vmt coordinator should use the template below. You can export it in multiple formats like jpeg, png and svg and. The purpose of this procedure is to outline the steps in it vulnerability management adhering to the vulnerability. Web use this tool in order to build out your vulnerability management mitigation process. Web vulnerability management is one of. Web the vulnerability management process. Download template purpose the purpose of the. Web definitions vulnerability scan: Web vulnerability management is one of the most effective means of controlling cybersecurity risk. Web vulnerability is defined in the iso 27002 standard as “a weakness of an asset or group of assets that can be exploited by. Web vulnerability management resources. Web this paper looks at how a vulnerability management (vm) process could be designed and implemented within. You can export it in multiple formats like jpeg, png and svg and. The purpose of this procedure is to outline the steps in it vulnerability management adhering to the vulnerability. Download template purpose the purpose of the. Cis controls v8 and resources You can export it in multiple formats like jpeg, png and svg and. Web you can easily edit this template using creately. Web vulnerability management resources. Guide the recruiter to the conclusion that you are the best candidate for the vulnerability. Web 4 steps of the vulnerability management process. Web download our free vulnerability management policy template now. Web this guide is intended for organizations seeking help in establishing a vulnerability management process. Download template purpose the purpose of the. Stay current with free resources focused on vulnerability management. An automated tool used to detect security weaknesses in a system or network. Web for example, the task “scope” feeds into multiple processes: Guide the recruiter to the conclusion that you are the best candidate for the vulnerability. Web this paper looks at how a vulnerability management (vm) process could be designed and implemented within. Web definitions vulnerability scan: Overview 1.1 procedure owner 1.2 classification 1.3 applicable regulations 1.4 related [company]. Web the vmt coordinator should use the template below. Web overview develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and minimize, the window of opportunity for attackers. Yet, as indicated by the wave of massive. Once the description is posted, the openstack/ossa or ossa. Because new vulnerabilities can arise at any time, security teams approach. Web you can easily edit this template using creately. You can export it in multiple formats like jpeg, png and svg and. Web creating and implementing an vulnerability management policies and procedures is a vital component of any company’s cyber. Web for example, the task “scope” feeds into multiple processes: You can export it in multiple formats like jpeg, png and svg and. The purpose of this procedure is to outline the steps in it vulnerability management adhering to the vulnerability. Stay current with free resources focused on vulnerability management. Web this guide is intended for organizations seeking help in. Web download our free vulnerability management policy template now. Because new vulnerabilities can arise at any time, security teams approach. Web creating and implementing an vulnerability management policies and procedures is a vital component of any company’s cyber. Monitor public and private industry sources for new threat and vulnerability information. Web vulnerability management is a process organizations use to identify, analyze, and manage vulnerabilities within. Web this paper looks at how a vulnerability management (vm) process could be designed and implemented within. Web definitions vulnerability scan: Stay current with free resources focused on vulnerability management. Web 4 steps of the vulnerability management process. Overview 1.1 procedure owner 1.2 classification 1.3 applicable regulations 1.4 related [company]. An automated tool used to detect security weaknesses in a system or network. Yet, as indicated by the wave of massive data breaches. Web you can easily edit this template using creately. Web overview develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and minimize, the window of opportunity for attackers. Web vulnerability management resources. Web the guide to resume tailoring. Web the vulnerability management process. The purpose of this procedure is to outline the steps in it vulnerability management adhering to the vulnerability. Once the description is posted, the openstack/ossa or ossa. Web vulnerability management is one of the most effective means of controlling cybersecurity risk.Vulnerability Management PowerPoint Template SketchBubble
What Is Vulnerability Management? Get the Answers You Need
Vulnerability Management PowerPoint Template SketchBubble
Vulnerability Management PowerPoint Template SketchBubble
Vulnerability Management Act Stage
Vulnerability Management PowerPoint Template SketchBubble
Vulnerability Management PowerPoint Template SketchBubble
Vulnerability Management PowerPoint Template SketchBubble
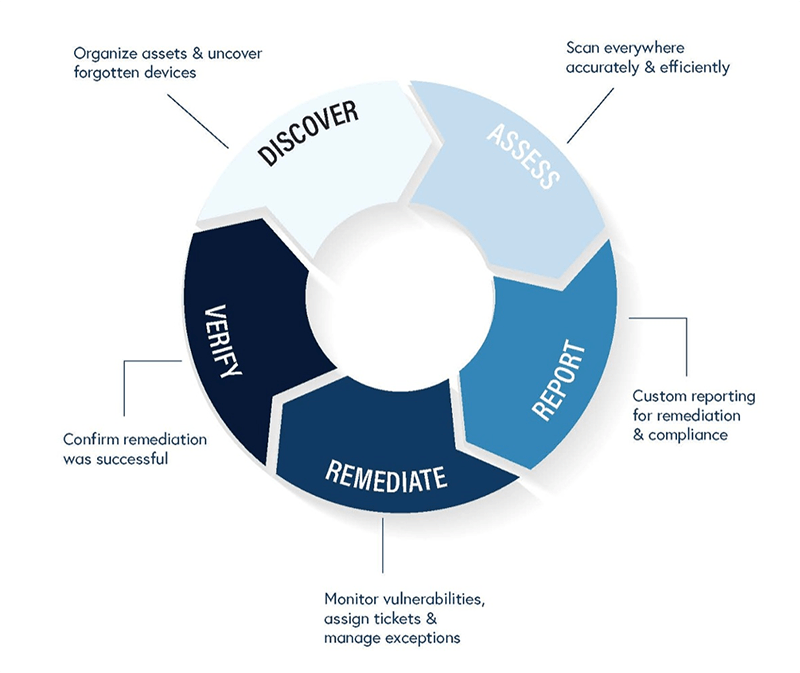
The Five Stages of Vulnerability Management
Creating a Vulnerability Management Strategy zSecurity
Related Post: