Vulnerability Scan Report Template
Vulnerability Scan Report Template - Web a vulnerability assessment report details the security weaknesses discovered in a vulnerability assessment. Web application vulnerability scanners are automated tools that scan web applications, normally from. Web this facility hazard vulnerability analysis template can be used regardless of the facility. Web the pci internal vulnerability scanning report presents extensive data about the vulnerability status of the. So, hop on over to. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in. Web pk !:€§÷ä · [content_types].xml ¢ ( ì—moô0 †ïhü‡èw´ñ¶ „ðf{àã •( w¯3é ü%{¶íþ{&é®auú ò´{‰”ììû>v {²º¸5:»† •³ ;ë. Web a scan report includes current vulnerability information about hosts in your account (hosts you select at run time). A different sheet is created for. Web vulnerability report contains a statistical data analysis for web vulnerabilities and network perimeter vulnerabilities. Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals and society. So, hop on over to. Web application vulnerability scanners are automated tools that scan web applications, normally from. Web a code injection vulnerability that afflicted atlassian confluence was the second most exploited cve in 2022. A vulnerability is a weakness. Web in tenable vulnerability management, the advanced agent scan template allows for two scanning methods: Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals and society. So, hop on over to. In the top navigation bar, click. Web a scan report includes current vulnerability information about hosts in your account (hosts. Web application vulnerability scanners are automated tools that scan web applications, normally from. Web vulnerability checks are not included. Web in tenable vulnerability management, the advanced agent scan template allows for two scanning methods: So, hop on over to. In the top navigation bar, click. Web every vulnerability should follow this template. A different sheet is created for. Web a code injection vulnerability that afflicted atlassian confluence was the second most exploited cve in 2022. Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of. Web it is good practice to identify the type of vulnerability. Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals and society. In the top navigation bar, click. A vulnerability is a weakness in an application (frequently a. Web pk !:€§÷ä · [content_types].xml ¢ ( ì—moô0 †ïhü‡èw´ñ¶ „ðf{àã •( w¯3é ü%{¶íþ{&é®auú ò´{‰”ììû>v {²º¸5:»† •³ ;ë. Web in tenable vulnerability management, the advanced. So, hop on over to. Web a code injection vulnerability that afflicted atlassian confluence was the second most exploited cve in 2022. Web a scan report includes current vulnerability information about hosts in your account (hosts you select at run time). Web to create a scan report: Web a vulnerability report is a document provided by security testers after the. Web a vulnerability report is a document provided by security testers after the assessment of a target’s security. Web ultimate the vulnerability report provides information about vulnerabilities from scans of the default branch. Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of. Web vulnerability checks are not included. Web this. Web a vulnerability report is a document provided by security testers after the assessment of a target’s security. A vulnerability is a weakness in an application (frequently a. Web this facility hazard vulnerability analysis template can be used regardless of the facility. Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals. Web pk !:€§÷ä · [content_types].xml ¢ ( ì—moô0 †ïhü‡èw´ñ¶ „ðf{àã •( w¯3é ü%{¶íþ{&é®auú ò´{‰”ììû>v {²º¸5:»† •³ ;ë. In the top navigation bar, click. Web vulnerability checks are not included. A different sheet is created for. Web to create a scan report: Web a code injection vulnerability that afflicted atlassian confluence was the second most exploited cve in 2022. Web to get a better understanding of the vulnerability assessment process, let’s take a look at the following four. Web a scan report includes current vulnerability information about hosts in your account (hosts you select at run time). Web creating a vulnerability assessment. Web in tenable vulnerability management, the advanced agent scan template allows for two scanning methods: Web a scan report includes current vulnerability information about hosts in your account (hosts you select at run time). Web the pci internal vulnerability scanning report presents extensive data about the vulnerability status of the. Web to create a scan report: Web application vulnerability scanners are automated tools that scan web applications, normally from. Web to get a better understanding of the vulnerability assessment process, let’s take a look at the following four. Web ultimate the vulnerability report provides information about vulnerabilities from scans of the default branch. The scan's results page appears. Web a vulnerability report is a document provided by security testers after the assessment of a target’s security. In the top navigation bar, click. Web creating a vulnerability assessment report involves analyzing an organization’s systems, diagnosing system vulnerabilities, and describing the severity of. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in. Web assessing a vulnerability and reporting on it can assist to reduce the danger it poses to individuals and society. Web a vulnerability assessment report details the security weaknesses discovered in a vulnerability assessment. Web vulnerability report contains a statistical data analysis for web vulnerabilities and network perimeter vulnerabilities. So, hop on over to. Web every vulnerability should follow this template. Web pk !:€§÷ä · [content_types].xml ¢ ( ì—moô0 †ïhü‡èw´ñ¶ „ðf{àã •( w¯3é ü%{¶íþ{&é®auú ò´{‰”ììû>v {²º¸5:»† •³ ;ë. A vulnerability is a weakness in an application (frequently a. Web this facility hazard vulnerability analysis template can be used regardless of the facility.
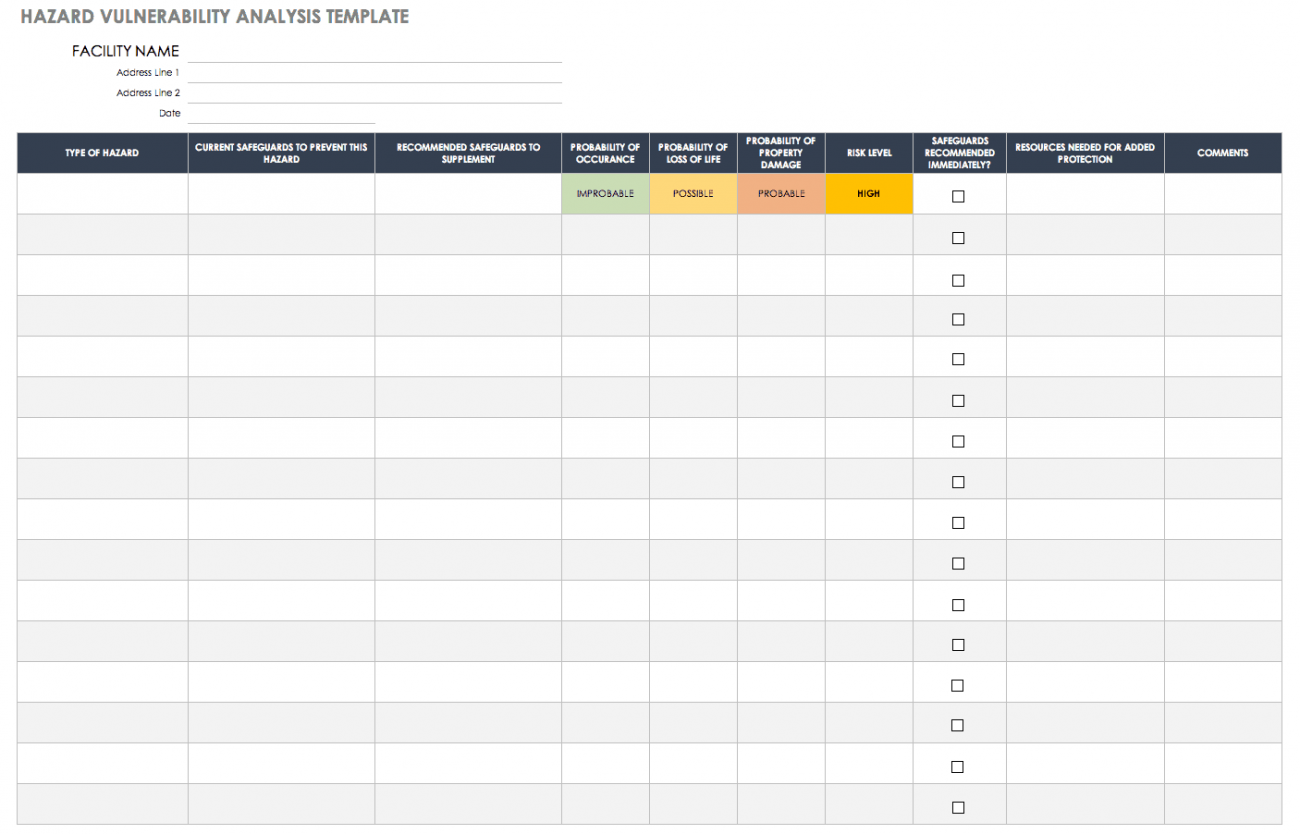
Free Vulnerability Assessment Templates Smartsheet
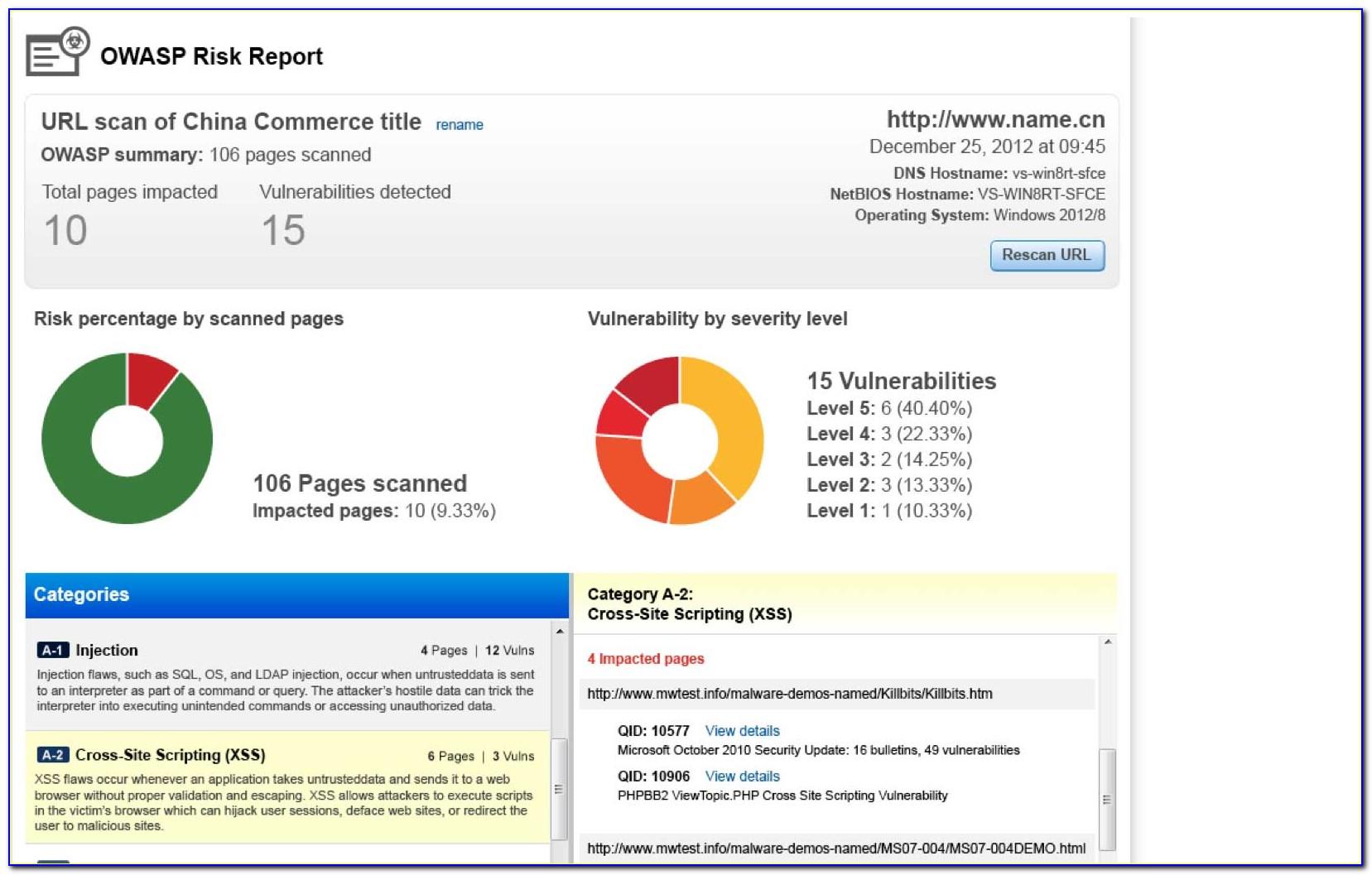
Network Vulnerability Scanning & Assessment Services PurpleSec
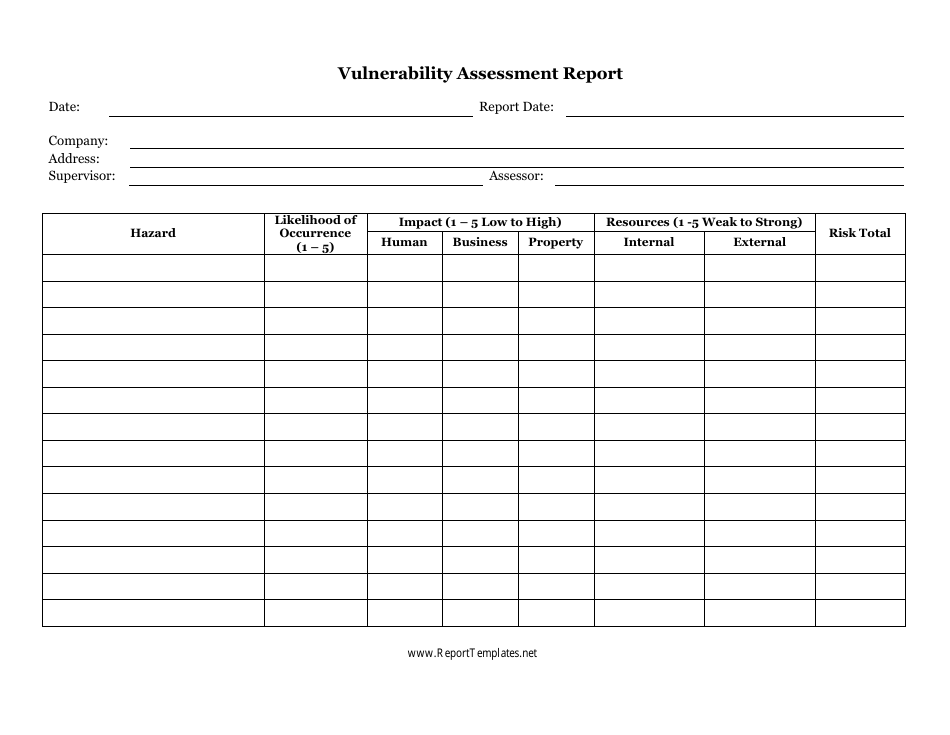
Vulnerability Assessment Report Template Download Printable PDF
Web Vulnerability Assessment Report Template Template Resume
Free Vulnerability Assessment Templates Smartsheet
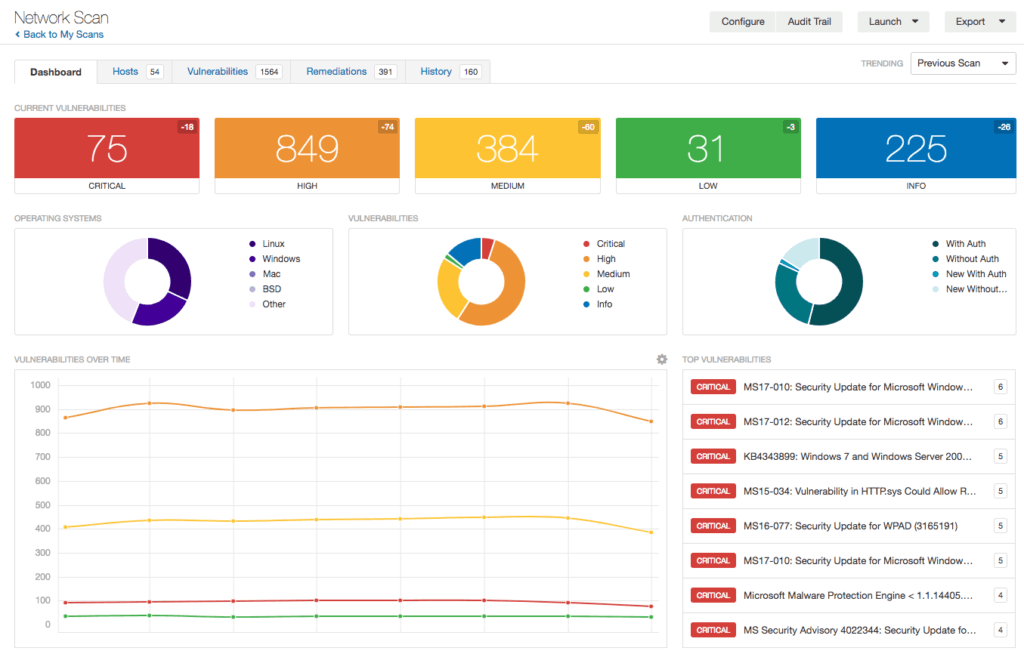
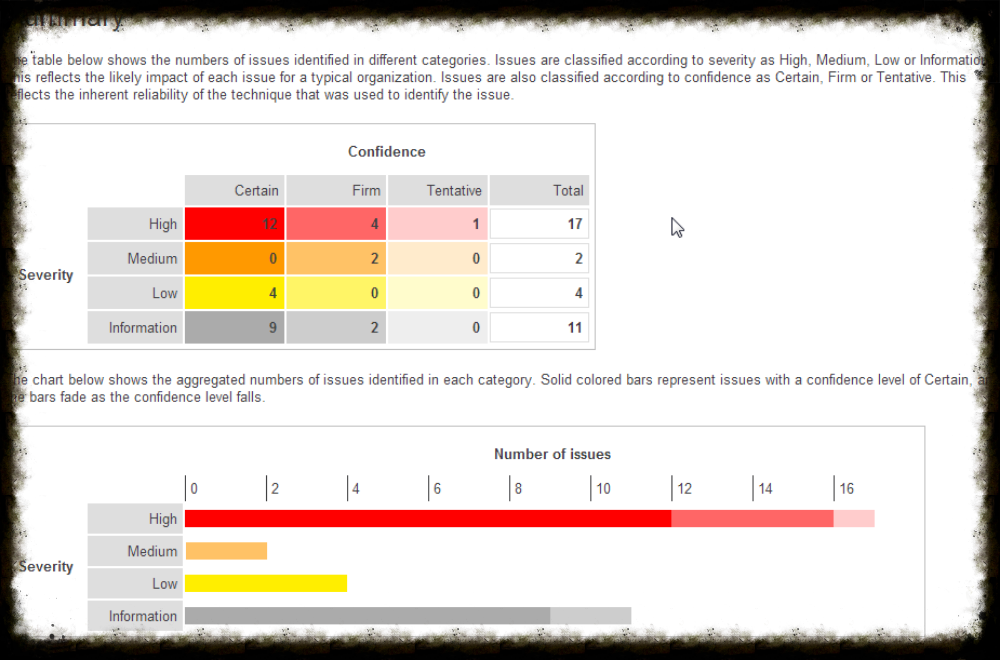
Analysing vulnerability scanning reports — Innovative
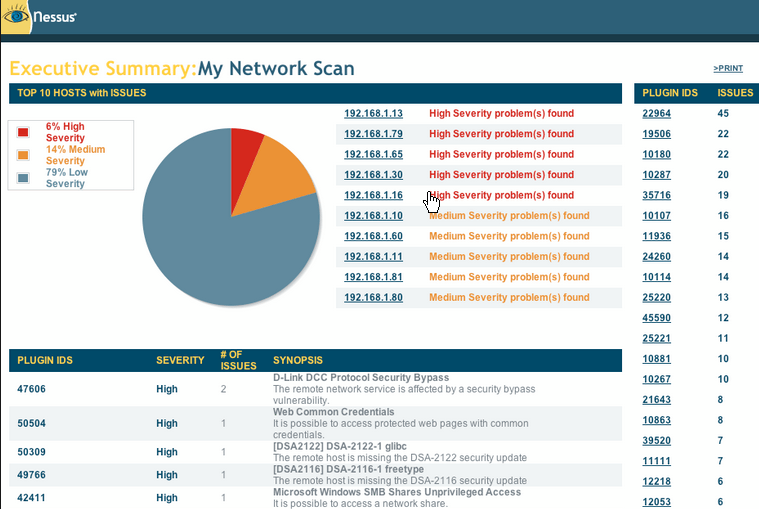
Windows Vulnerability Summary Report SC Report Template Tenable®
Pocketin Sample Risk Assessment Report 31 Risk Assessment Templates In
Vulnerability scanning Blue Lance
Related Post: